Identity Access Management
All API calls between AWS services must be authenticated.
Two places where this is used:
- Access to AWS accounts
- Access between AWS services
Concepts
- Authentication you are who you say you are
- Authorisation what you have permission to do
IAM
Global configuration not specific to any Region.
Is made up of IAM Users, IAM Groups, IAM Roles and IAM Policies as outlined below.
IAM User
A unique user account.
Has associated username and password as well as well as security keys (for programmatic access).
IAM Policy
What a IAM User or IAM Group is authorised to do.
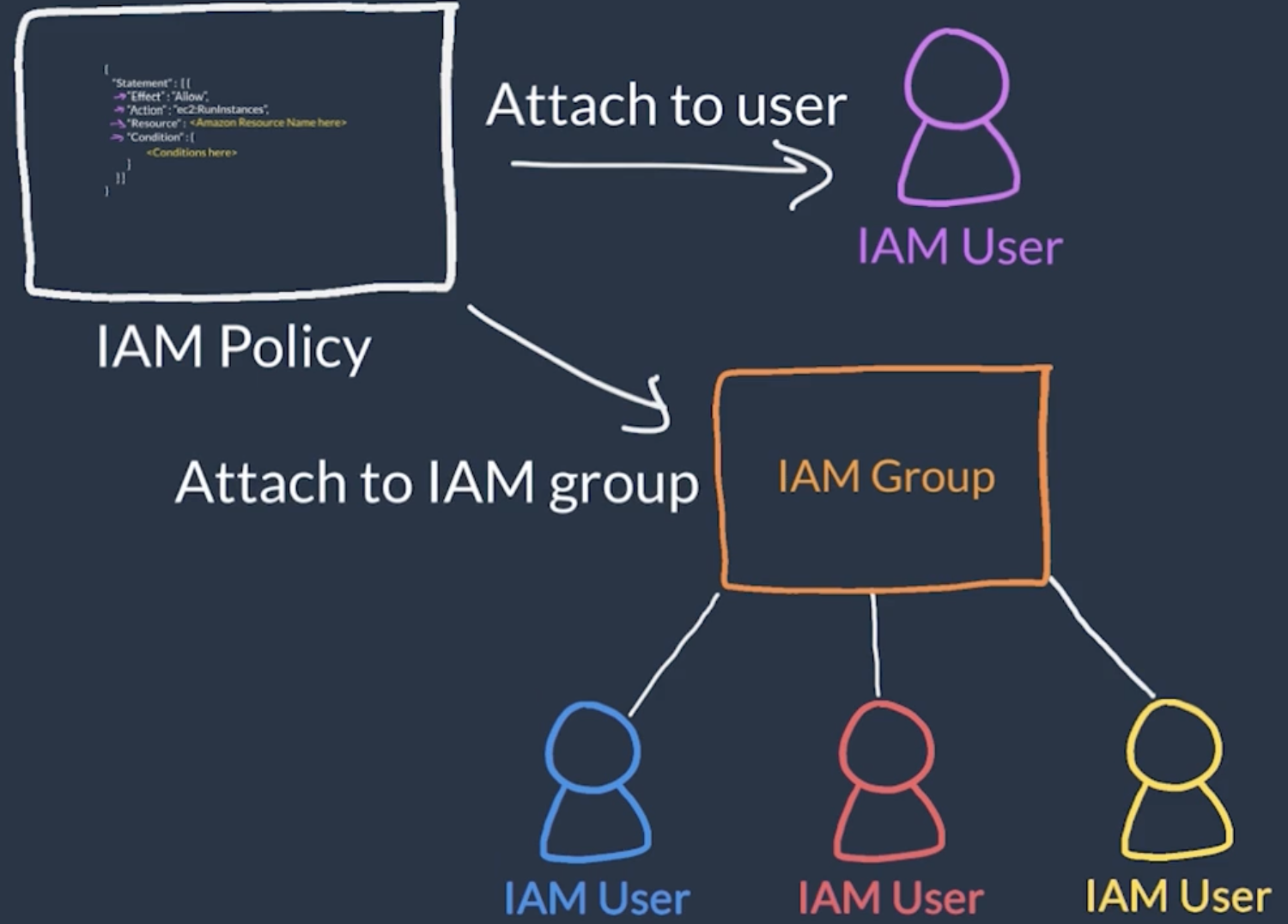
Applying policies to an IAM Group is preferred over an IAM User
A policy comprises an
- effect allow or deny
- action the allowed API calls e.g. `ec2:*
- resources the resources where these policies apply
- condition further restrictions
You can define customer policies or use AWS managed policies which are predefined.
IAM Role
A IAM Role is a role that can be assumed by an IAM User or thing.
Unlike an IAM User an IAM Role has no static logic credentials instead:
- They are assumed programmatically
- Credentials are temporary
- Credentials expire and are rotated.
Services are created with IAMRoles that they can assume.
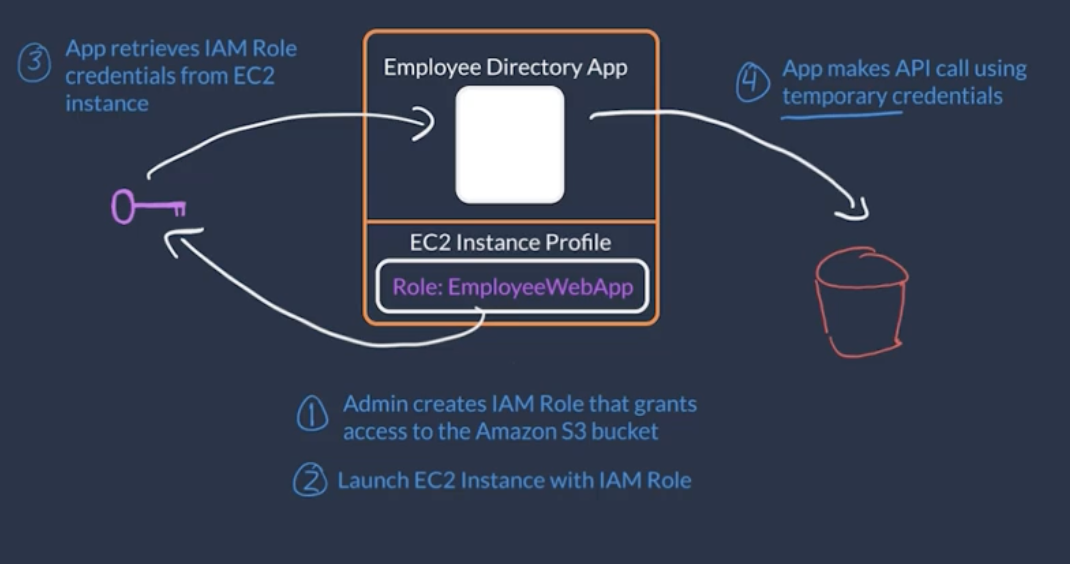
Creating an IAM Role
Associate the IAM Role with:
- Who is allowed to assume the role (e.g.
EC2)
- IAMPolicies
- Tags, ket value pairs useful for billing and resource management
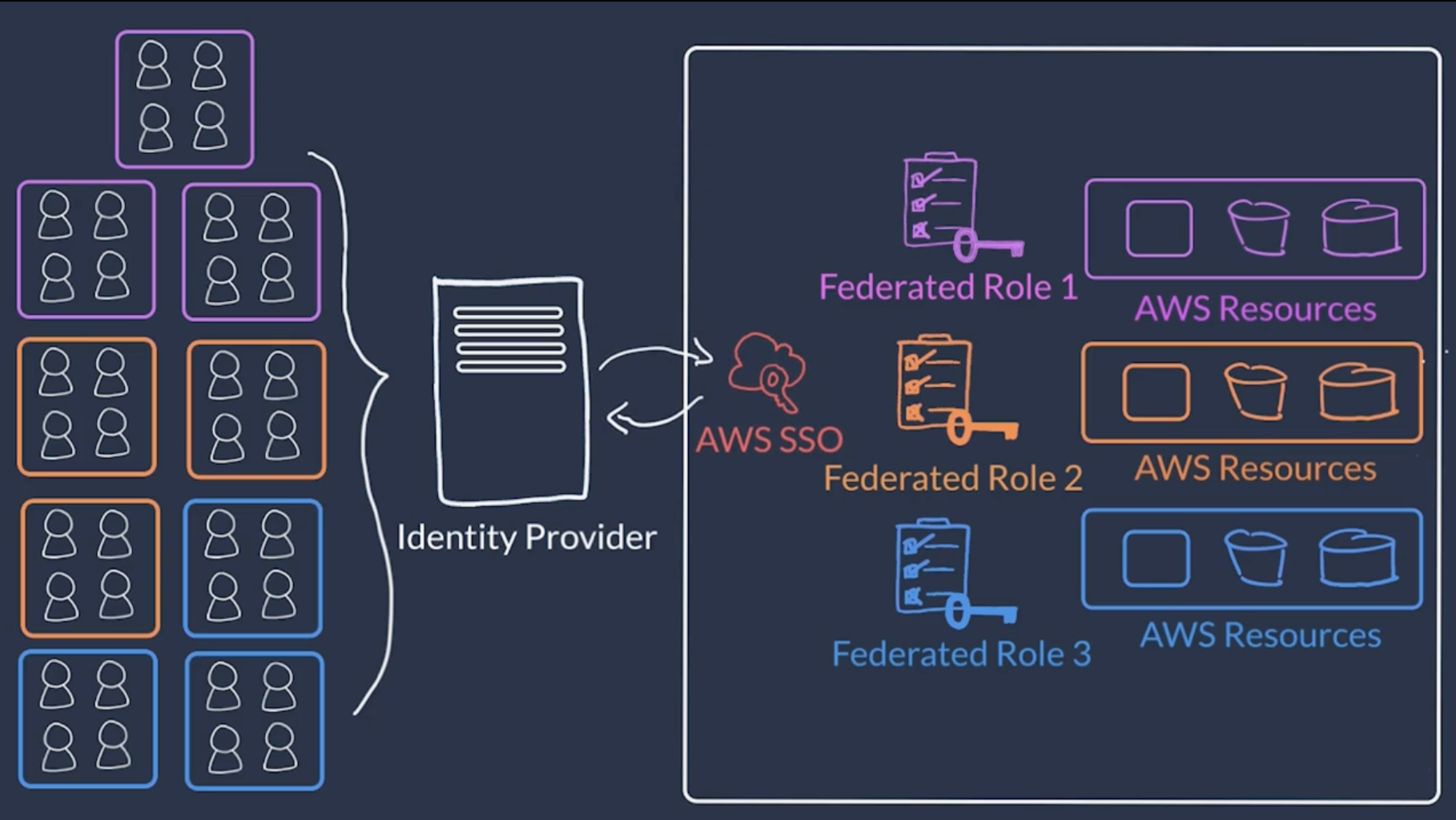
Identity Providers
External identity providers can assume IAM Roles, to assign roles to users, these are known as federated users.